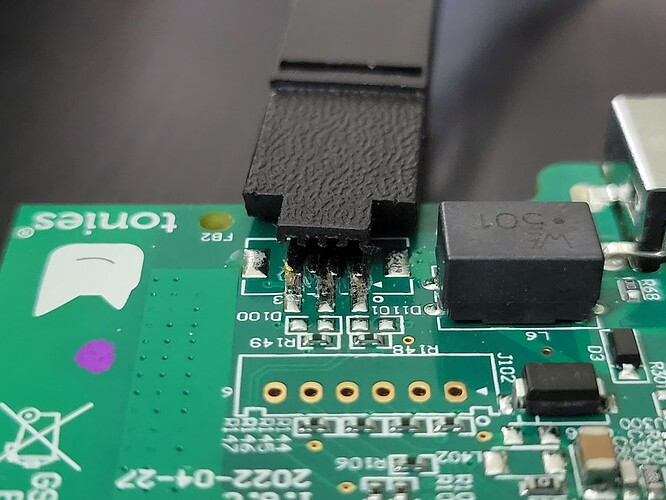
Thank you for your effort! What do you use to shorten the J100 Jumper? I only know the jumpers on mainboards, which have pins?
Curved tweezers, but anything that conducts electricity works
If you are able to solder, i would recomment to solder a 2-pin pin header to J100.
Then you can use a common jumper to close it.

During normal operation you put the jumper to a singel pin only.
Isn’t this a little overload? Normally you don’t use this jumper regularly
I am currently in the process of getting docker-compose up and running.
The first time the page is called up, the message “Select certificate” appears. There I get a suggestion from MS-Organization-Access. When I select this, the following message appears.
Now the following message appears in the browser:
Error 401
Unauthorized
The logs show the following:
INFO |server.c:0701:server_init| 2 open HTTPS connections
WARN |tls_server_fsm.c:0260:tlsPerformServerHandshake| TLS handshake failure!
INFO |server.c:0701:server_init| 1 open HTTPS connections
WARN |server_helpers.c:0817:httpServerUriUnauthorizedCallback| >> 401 on index.shtm
With http via port 80 it works without any problems.
Hi,
Besides disabling http only you should also disable https auth cert. Then it should work fine.
Thanks for that guide.
I‘m having a weird problem: When downloading the dump via browser or via esptool. The connction times out randomly during the dump. I already replaced/resoldered the UART wires and replaced the UART/USB Adapter with a second brand. Serial monitor connects without any problem.
I nearly did 20 runs to finally get one complete
dump. Interesting side fact, I was only able to connect @ bautrate 115200.
I‘m now a bit worried to overwrite the flash as you might imagine.
Anyone a clue what could be the cause and how I could get rid off?
> esptool.py -b 115200 --port /dev/cu.usbserial-110 read_flash 0x0 0x80000 tb.esp32.bin
esptool.py v4.7.0
Serial port /dev/cu.usbserial-110
Connecting....
Detecting chip type... ESP32-S3
Chip is ESP32-S3 (QFN56) (revision v0.2)
Features: WiFi, BLE
Crystal is 40MHz
MAC: 3c:84:27:02:bb:ac
Uploading stub...
Running stub...
Stub running...
118784 (22 %)
A fatal error occurred: Corrupt data, expected 0x1000 bytes but received 0xfba bytes
You tried a different USB port or computer?
How you power your box?
Not yet, I trusted the power of Apple ![]()
Will try another PC.
Start order:
- UART Adapter Connected to the Toniebox
- UART Adapter to PC
- Tonie to Power Connecter
All other peripherals and battery are disconnected
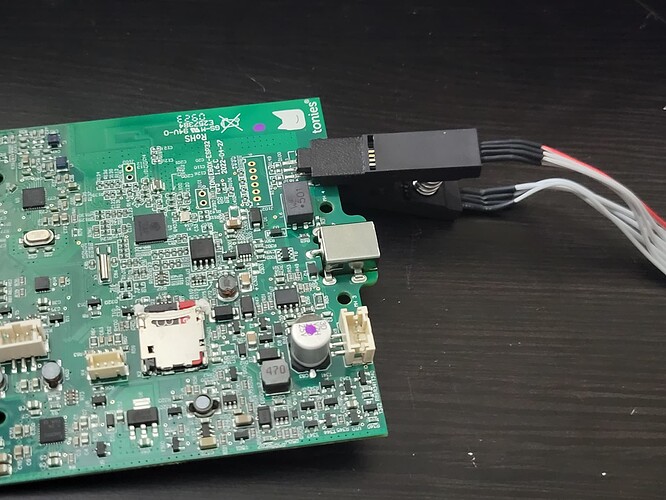
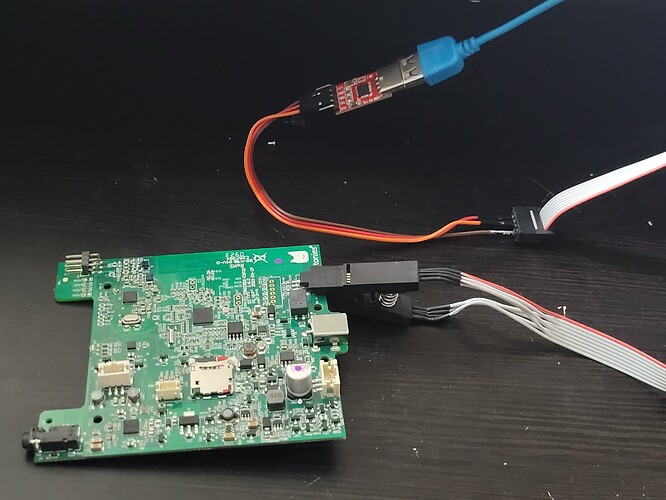
So just to drop this here that may help some of you with issues connecting UART to the board:
WWZMDiB EEPROM Programmer & CH341A Programmer (CH341A + SOIC8 Clip + Dual Conversion Plate Amazon.com
No need to solder, especially for something you probably only need to do once or twice.
UART sold separately
It it really an issue with the MacBook….
Successfully first try dump on the windows machine (after adapter driver installation, reboot, and bitlocker and windows recovery key query……)
Thanks for the hints and help!
Just so everyone can see the clamp kit I recommended in action. It works well, I’ve flashed 2 boxes so far:
Great, this clamp is dual use. UART + Flash SOP8
Hi, I’m stuck at extracting the certificates. I followed the doc and downloaded the bin. When I run teddycloud ESP32CERT extract data/firmware/ESP32_mac_ 1.bin certs/client /certs/client stays empty and I get this output:
root@teddycloud:/teddycloud# teddycloud ESP32CERT extract data/firmware/ESP32_mac_1.bin certs/client/
TeddyCloud vX.X.X (9572d62) - 2024-07-06 19:24:58 +0000 ubuntu linux-x86_64(64)
INFO |settings.c:0779:settings_load_ovl()| Load settings from /teddycloud/config/config.overlay.ini
INFO |settings.c:0779:settings_load_ovl()| Load settings from /teddycloud/config/config.ini
INFO |tls_adapter.c:0208:read_certificate()| File '/teddycloud/certs/server/ca-root.pem' assumed PEM style
INFO |tls_adapter.c:0205:read_certificate()| File '/teddycloud/certs/server/ca-key.pem' detected as DER style RSA PRIVATE KEY
INFO |tls_adapter.c:0208:read_certificate()| File '/teddycloud/certs/server/teddy-cert.pem' assumed PEM style
INFO |tls_adapter.c:0205:read_certificate()| File '/teddycloud/certs/server/teddy-key.pem' detected as DER style RSA PRIVATE KEY
ERROR|tls_adapter.c:0193:read_certificate()| Failed to open '/teddycloud/certs/client/ca.der' for cert type detection
ERROR|tls_adapter.c:0380:load_cert()| Loading cert '/teddycloud/certs/client/ca.der' failed
ERROR|tls_adapter.c:0193:read_certificate()| Failed to open '/teddycloud/certs/client/client.der' for cert type detection
ERROR|tls_adapter.c:0380:load_cert()| Loading cert '/teddycloud/certs/client/client.der' failed
ERROR|tls_adapter.c:0193:read_certificate()| Failed to open '/teddycloud/certs/client/private.der' for cert type detection
ERROR|tls_adapter.c:0380:load_cert()| Loading cert '/teddycloud/certs/client/private.der' failed
INFO |settings.c:0779:settings_load_ovl()| Load settings from /teddycloud/config/config.overlay.ini
INFO |tls_adapter.c:0394:tls_adapter_init()| Loading certificates...
INFO |tls_adapter.c:0208:read_certificate()| File '/teddycloud/certs/server/ca-root.pem' assumed PEM style
INFO |tls_adapter.c:0205:read_certificate()| File '/teddycloud/certs/server/ca-key.pem' detected as DER style RSA PRIVATE KEY
INFO |tls_adapter.c:0208:read_certificate()| File '/teddycloud/certs/server/teddy-cert.pem' assumed PEM style
INFO |tls_adapter.c:0205:read_certificate()| File '/teddycloud/certs/server/teddy-key.pem' detected as DER style RSA PRIVATE KEY
ERROR|tls_adapter.c:0193:read_certificate()| Failed to open '/teddycloud/certs/client/ca.der' for cert type detection
ERROR|tls_adapter.c:0380:load_cert()| Loading cert '/teddycloud/certs/client/ca.der' failed
ERROR|tls_adapter.c:0193:read_certificate()| Failed to open '/teddycloud/certs/client/client.der' for cert type detection
ERROR|tls_adapter.c:0380:load_cert()| Loading cert '/teddycloud/certs/client/client.der' failed
ERROR|tls_adapter.c:0193:read_certificate()| Failed to open '/teddycloud/certs/client/private.der' for cert type detection
ERROR|tls_adapter.c:0380:load_cert()| Loading cert '/teddycloud/certs/client/private.der' failed
ERROR|server.c:0627:server_init()| httpServerInit() for HTTP failed with code 1
=================================================================
==161==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 936 byte(s) in 1 object(s) allocated from:
#0 0x564f01e8aa67 in __interceptor_malloc (/usr/local/bin/teddycloud+0x657a67)
#1 0x564f0238aff2 in socketOpen src/platform/platform_linux.c:48
#2 0x564f0210af21 in httpServerInit src/cyclone/cyclone_tcp/http/http_server.c:169
#3 0x564f01f8057b in server_init src/server.c:624
#4 0x564f01df4f0d in main src/main.c:567
#5 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
Direct leak of 451 byte(s) in 16 object(s) allocated from:
#0 0x564f01e8aa67 in __interceptor_malloc (/usr/local/bin/teddycloud+0x657a67)
#1 0x564f01f82711 in custom_asprintf src/server_helpers.c:39
#2 0x564f01f70180 in mqtt_init src/mqtt.c:947
#3 0x564f01df4ee0 in main src/main.c:566
#4 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
Direct leak of 367 byte(s) in 16 object(s) allocated from:
#0 0x564f01e8aa67 in __interceptor_malloc (/usr/local/bin/teddycloud+0x657a67)
#1 0x564f01f675bb in mqtt_topic_str src/mqtt.c:86
#2 0x564f01f701e2 in mqtt_init src/mqtt.c:949
#3 0x564f01df4ee0 in main src/main.c:566
#4 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
Direct leak of 351 byte(s) in 16 object(s) allocated from:
#0 0x564f01e8aa67 in __interceptor_malloc (/usr/local/bin/teddycloud+0x657a67)
#1 0x564f01f675bb in mqtt_topic_str src/mqtt.c:86
#2 0x564f01f701b1 in mqtt_init src/mqtt.c:948
#3 0x564f01df4ee0 in main src/main.c:566
#4 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
Direct leak of 191 byte(s) in 16 object(s) allocated from:
#0 0x564f01e8aa67 in __interceptor_malloc (/usr/local/bin/teddycloud+0x657a67)
#1 0x564f01f67431 in mqtt_settingname_clean src/mqtt.c:58
#2 0x564f01f700fd in mqtt_init src/mqtt.c:945
#3 0x564f01df4ee0 in main src/main.c:566
#4 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
Direct leak of 1 byte(s) in 1 object(s) allocated from:
#0 0x564f01e31ba7 in __interceptor_strdup (/usr/local/bin/teddycloud+0x5feba7)
#1 0x564f01f80512 in server_init src/server.c:621
#2 0x564f01df4f0d in main src/main.c:567
#3 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
Direct leak of 1 byte(s) in 1 object(s) allocated from:
#0 0x564f01e31ba7 in __interceptor_strdup (/usr/local/bin/teddycloud+0x5feba7)
#1 0x564f01f80362 in server_init src/server.c:613
#2 0x564f01df4f0d in main src/main.c:567
#3 0x7f1329b47d8f (/lib/x86_64-linux-gnu/libc.so.6+0x29d8f)
SUMMARY: AddressSanitizer: 2298 byte(s) leaked in 67 allocation(s).
root@teddycloud:/teddycloud# teddycloud ESP32CERT extract data/firmware/ESP32_mac_1.bin certs/client
TeddyCloud vX.X.X (9572d62) - 2024-07-06 19:24:58 +0000 ubuntu linux-x86_64(64)
I downloaded the bin several times via the webinterface and with esptool but it’s always the same when extracting ther certificates. Whats wrong here?
The guide uses an outdated syntax, please follow the original guide
Thank you for pointing this out! I got the certs now ![]()
Hey all,
I guess I am somehow stupid… I got the cloud up and running on my synology nas, I got the clamp attached so that I can read the serial information but what I do not get done is “short the jumper J100”. I put a cable in to connect the J100 with the whole next to it but it still starts in “SPI_FAST_FLASH_BOOT” mode and I do not get why. I tried multiple cables already so that I am sure that this is not the case.
Any idea what I could do?