Hello, my Toniebox 1 didn’t worked anymore so I returned it in warranty and I was refunded, so I bought a Toniebox 2. I was quite surprised to notice that emulating .nfc with the Flipper would stop after 2 mins.
At first I though they implemented some anti-piracy protection.
But actually… it is the opposite. They removed the privacy protection. I was surprised I could read the paw patrol game without auth as Tommybox.
I think they had to do it because of the new games. I think they have several antenna’s and they make some polling between them because in the game you have more than one NFC. And I think with privacy mode it was impossible.
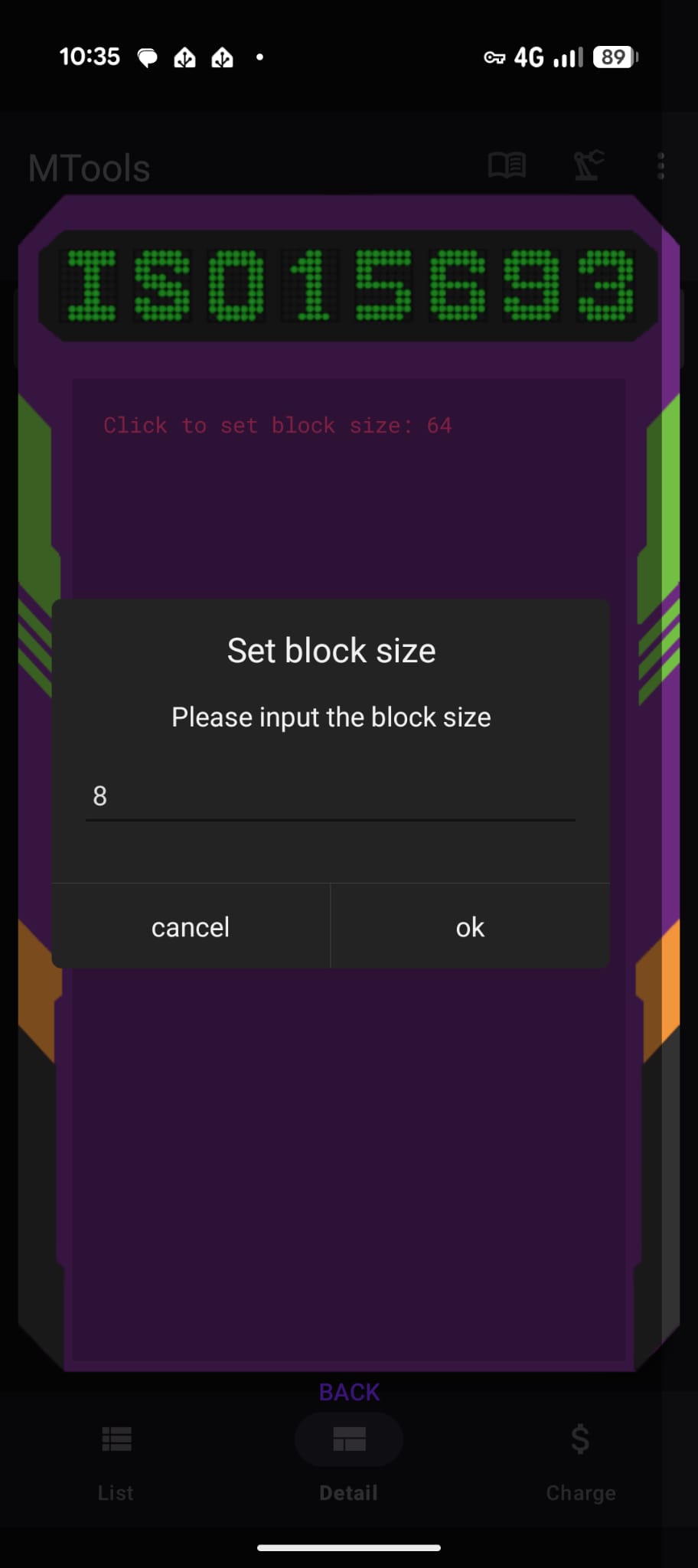
I tried a Magic SLI card from Aliexpress I had lying around, changed block size, copied UID and data from a .nfc (the new Hotwheels) and it worked. Amazing… I hope they won’t patch it ![]()

I don’t have Proxmod so I used an Android app called Mtools.
Then I was ok so I just have to edit the .nfc files to “convert” them to ISO15693 … but it is still crashing after 2 mins with the flipper! I tried to copy exactly my magic card with the Flipper but he reads only 0’s, he can’t handle the modifiable block size.
Why does the Toniebox still reads original Tonies that have privacy ? of course they have a legacy mode but I guess they made small changes on the timing, very tiny changes where the flipper doesn’t ACK with the exact timing required anymore.
For anyone interested, the dump of the paw patrol game is below (I replace some characters with X’s).
If anyone as an idea to make the Flipper work again let me know!
Filetype: Flipper NFC device
Version: 4
Device type can be ISO14443-3A, ISO14443-3B, ISO14443-4A, ISO14443-4B, ISO15693-3, FeliCa, NTAG/Ultralight, Mifare Classic, Mifare Plus, Mifare DESFire, SLIX, ST25TB, NTAG4xx, Type 4 Tag, EMV
Device type: SLIX
UID is common for all formats
UID: E0 04 01 09 10 9F XX XX
ISO15693-3 specific data
Data Storage Format Identifier
DSFID: 00
Application Family Identifier
AFI: 00
IC Reference - Vendor specific meaning
IC Reference: 01
Lock Bits
Lock DSFID: false
Lock AFI: false
Number of memory blocks, valid range = 1..256
Block Count: 80
Size of a single memory block, valid range = 01…20 (hex)
Block Size: 04
Data Content: XX XX 2D 37 B6 D1 47 3C A4 01 30 76 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block Security Status: 01 = locked, 00 = not locked
Security Status: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
SLIX specific data
SLIX capabilities field affects emulation modes. Possible options: Default, AcceptAllPasswords
Capabilities: Default
Passwords are optional. If a password is omitted, a default value will be used
Password Read: 00 00 00 00
Password Write: 00 00 00 00
Password Privacy: 0F 0F 0F 0F
Password Destroy: 0F 0F 0F 0F
Password EAS: 00 00 00 00
This is the card’s secp128r1 elliptic curve signature. It can not be calculated without knowing NXP’s private key.
Signature: XX XX B0 AB 93 E4 07 5F B8 E9 F6 D8 C3 17 65 97 65 0E D8 01 BF 3A F4 BA 8E 04 C6 F5 51 0F ED 79
Privacy Mode: false
Protection pointer configuration
Protection Pointer: 00
Protection Condition: 00
SLIX Lock Bits
Lock EAS: false
Lock PPL: falsestrong text
If you want proof emulate this file :
Filetype: Flipper NFC device
Version: 4
Device type can be ISO14443-3A, ISO14443-3B, ISO14443-4A, ISO14443-4B, ISO15693-3, FeliCa, NTAG/Ultralight, Mifare Classic, Mifare Plus, Mifare DESFire, SLIX, ST25TB, NTAG4xx, Type 4 Tag, EMV
Device type: ISO15693-3
UID is common for all formats
UID: E0 04 03 50 1A 89 17 CB
ISO15693-3 specific data
Data Storage Format Identifier
DSFID: 00
Application Family Identifier
AFI: 00
IC Reference - Vendor specific meaning
IC Reference: 8B
Lock Bits
Lock DSFID: false
Lock AFI: false
Number of memory blocks, valid range = 1..256
Block Count: 8
Size of a single memory block, valid range = 01…20 (hex)
Block Size: 04
Data Content: F3 58 92 32 CA CD 50 48 DD CE 99 F2 98 D8 FF 00 27 4F D2 CF 22 7B EA 67 C2 40 DF 79 F5 1C 50 BF
Block Security Status: 01 = locked, 00 = not locked
Security Status: 00 00 00 00 00 00 00 00
It will play for 30 secs