Sorry for the confusion. I’m just trying to provide as much info as possible.
Yes, I always get “owl” after flashing the patched firmware.
For the flashing process:
I’m pretty much just following the guide:
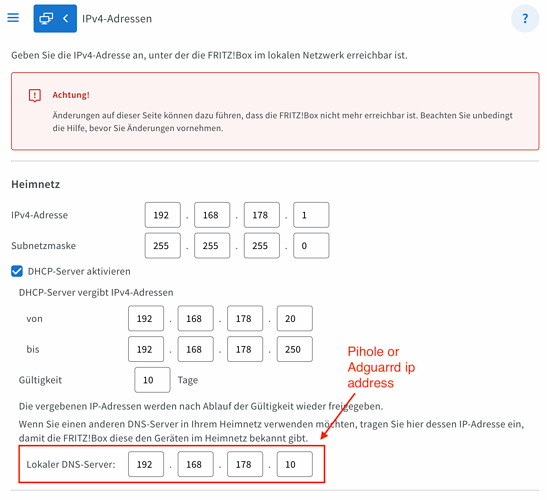
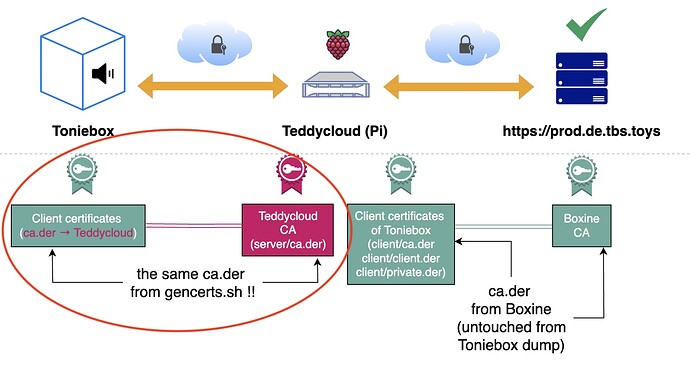
Creating Certs:
cd && mkdir toniebox && cd toniebox
wget "https://raw.githubusercontent.com/toniebox-reverse-engineering/teddycloud/master/contrib/gencerts.sh" -O gencert.sh
chmod 755 gencert.sh
./gencert.sh # -> faketime error
sudo apt install faketime
./gencert.sh # -> again, but this time its working and in comparison to the teddycloud cert creation, pretty fast
then I’m copying these to the teddycloud, but with sudo, because otherwise I did receive an error:
sudo docker cp ~/toniebox/certs/server/ca.der teddycloud:/teddycloud/certs/server/ca.der
sudo docker cp ~/toniebox/certs/server/ca-key.pem teddycloud:/teddycloud/certs/server/ca-key.pem
sudo docker cp ~/toniebox/certs/server/ca-root.pem teddycloud:/teddycloud/certs/server/ca-root.pem
sudo docker restart teddycloud
Then doing a cd certs which is a small detail missing in the guide, I think.
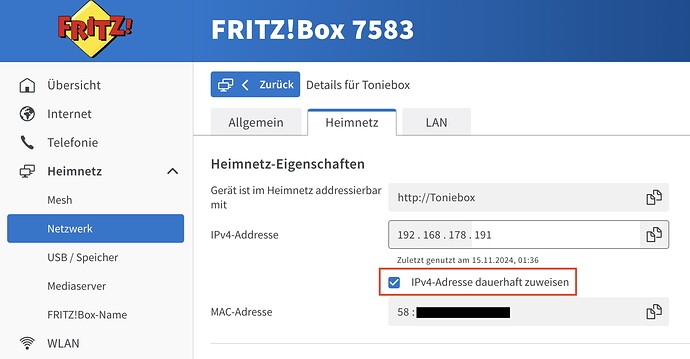
Then I’m extracting the firmware from the box with:
sudo flashrom -p ch341a_spi -r backupCC3235.bin
Confirm the 4mb and Boxine Sigings.
Then extracting in virtual environment:
pi@raspi:~/toniebox/certs $ source ~/.venv/bin/activate
pi@raspi:~/toniebox/certs $ cc3200tool -if backupCC3235.bin -d cc32xx read_all_files extract/
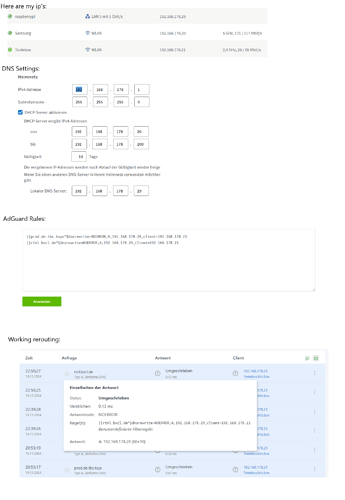
I Copy the extracted certs to teddycloud (I can confirm that I am able to connect to Boxine cloud)
Then I’m patching the firmware with the given command, again in virtual environment (My username is pi, too) And I’m flashing with “sudo flashrom -p ch341a_spi -w cc3235-flash.customca.bin”
That is my flashing process. I have the exact same CH341A programmer bought as mentioned in the beginning.
I just did a factory reset on my pi and my router and reflashed my teddybox with the backup. I’m thinking about doing a small video with my process, maybe someone can find out what I’m doing wrong. I already feel bad to spam this section…